The European General Data Protection Regulation (GDPR) has been in effect since May 25, 2018. In addition to the creation of:
- Privacy policies
- Records of processing activities
- Data Processing Agreements (DPAs)
The controller must also define the technical and organizational measures.
What is the purpose of technical and organizational measures?
The technical and organizational measures ensure that personal data processed by the controller is protected from unauthorized access in both IT systems and physical records.
The scope of the measures depends on various factors:
- The number of data / affected individuals
- The purpose of the processing,
- The likelihood of a risk occurring
- The impact on an individual in the event of harm
Which data needs to be protected?
The EU GDPR stipulates that all personal data must be identified and subjected to a risk analysis in accordance with Article 32(1) of the GDPR. Special categories of personal data must be protected with enhanced measures.
The different likelihood and severity of the risk to the rights and freedoms of a natural person must be assessed.
Which measures must be implemented for which systems?
To determine this, a list of all IT systems is required.
In which IT systems is personal data stored?
Is there a distinction for special categories of personal data?
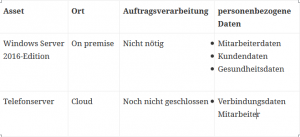
The risk analysis is conducted using the factors of the CIA triad.
carried out.
- C – Confidential
Confidentiality: Information may only be read by previously authorized users. - I – Integrity
Integrity: Refers to ensuring the accuracy of the data. - A – Availability
Availability: IT systems should be operational at all times.
How do I create a risk analysis?
The selected assets (company values) are now considered according to the criteria.
- Access Control
Building perimeter
Video surveillance
Locked office
Electronic access control - Access Protection
Authentication methods
Network segmentation
Personalized access
Firewall
Antivirus software - Access Control
Authorization concept
Complex passwords - Separation Control
Multi-tenancy capability - Transfer Control
Encryption options
Email encryption - Input Control
Logging - Availability
Disaster recovery plan
Backups
Redundant power supply design - Review/Assessment
Regular technical and organizational system audits - Data Processing
Written instructions from the client
Now, based on the current values, a scenario is developed in which the exploitation of a technical vulnerability or the absence of an organizational instruction within the company could lead to an unintended data release.
The likelihood of the scenario occurring is assessed, as well as the extent of the damage in the event it happens. The resulting calculated risk provides information about the personnel and financial resources needed to enhance the protection of the data.
Example: Risk Analysis
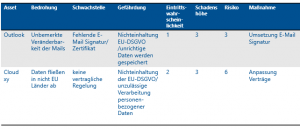
Do all measures have to be implemented?
The measures identified in the risk analysis are now evaluated, assigned, and time-limited in the action list.
This action list provides the authority with information about everything you have planned. Reasons are described in the action list.
Warum ist es nicht zur Umsetzung gekommen?
Warum findet die Umsetzung erst in 2 Jahren statt.
Die technischen Maßnahmen wie:
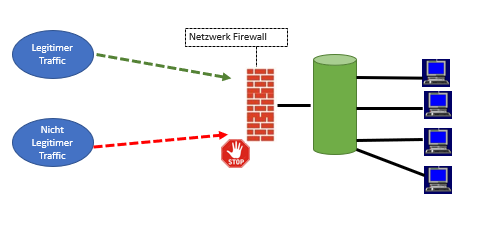
- Firewall
- Virensoftware
- Intrusion Detection System
- Mobile Device Management
- Remote Monitoring Management
- Backup Konzept
can be tested and implemented in cooperation with your IT system house.
The organizational measures are presented in the data protection management system. They cover the following topics:
- Handling of personal data
- Handling of mobile devices
- Internet usage
- Working from home
- Protection of devices while traveling
- Clean desk policy
- Deletion of data carriers
Standard Data Protection Model
The Standard Data Protection Model is a method with which technical and organizational measures can be established. The following measures can be generated from this model:
Technical measures:
- Structural changes to implement physical security
- Changes to the network infrastructure or outsourcing of data
- Video surveillance
- Access control system
- Firewall
- Intrusion Detection System (IDS)
- Antivirus software
- Commissioning of a logging server
- Implementation of encryption methods
The implementation of the measures can be carried out by in-house system administrators or by an external service provider, in compliance with the principles of "privacy by design" and "privacy by default."
Organizational measures are:
- Introduction of an information security policy
- Implementation of a training concept
- Process definition for granting access permissions
- Development of an authorization concept
- Process for managing cryptographic keys
- Guidelines for the disposal/removal of operating resources
- Change management
- Vulnerability management
- Process for responding to data security incidents
- Compliance and continuous improvement as well as conformity of your data security management system
The organizational measures should be reviewed annually by an independent auditor. However, it is not necessary to involve an accredited body for an official certification.
Get in touch without obligation and let’s talk:
- Email: info@kvinne.de
- Tel: +49.351.21971182
We look forward to hearing from you!

